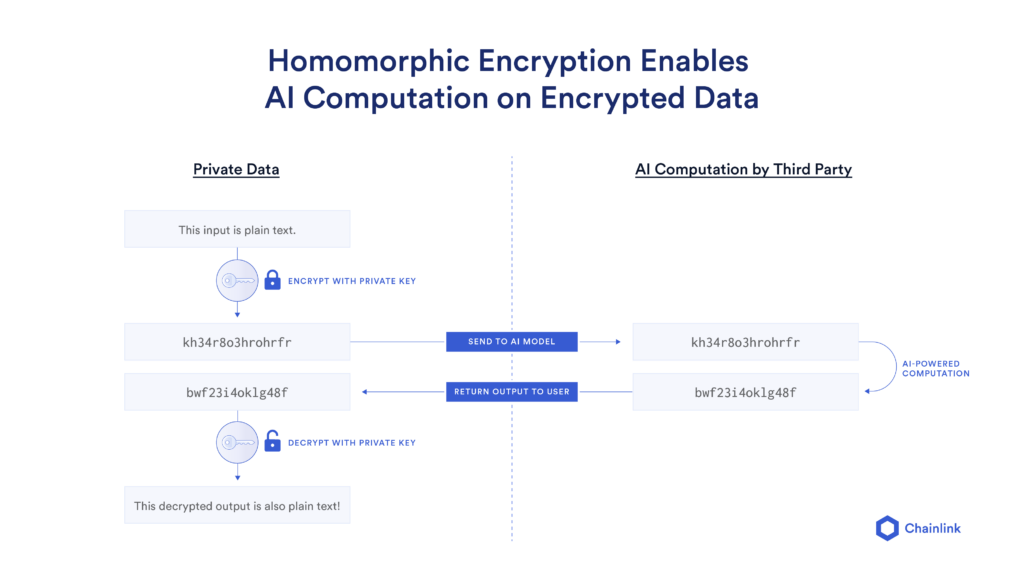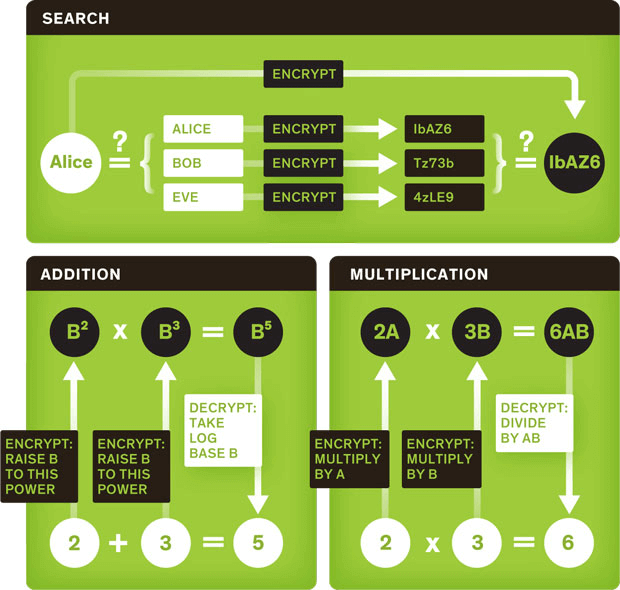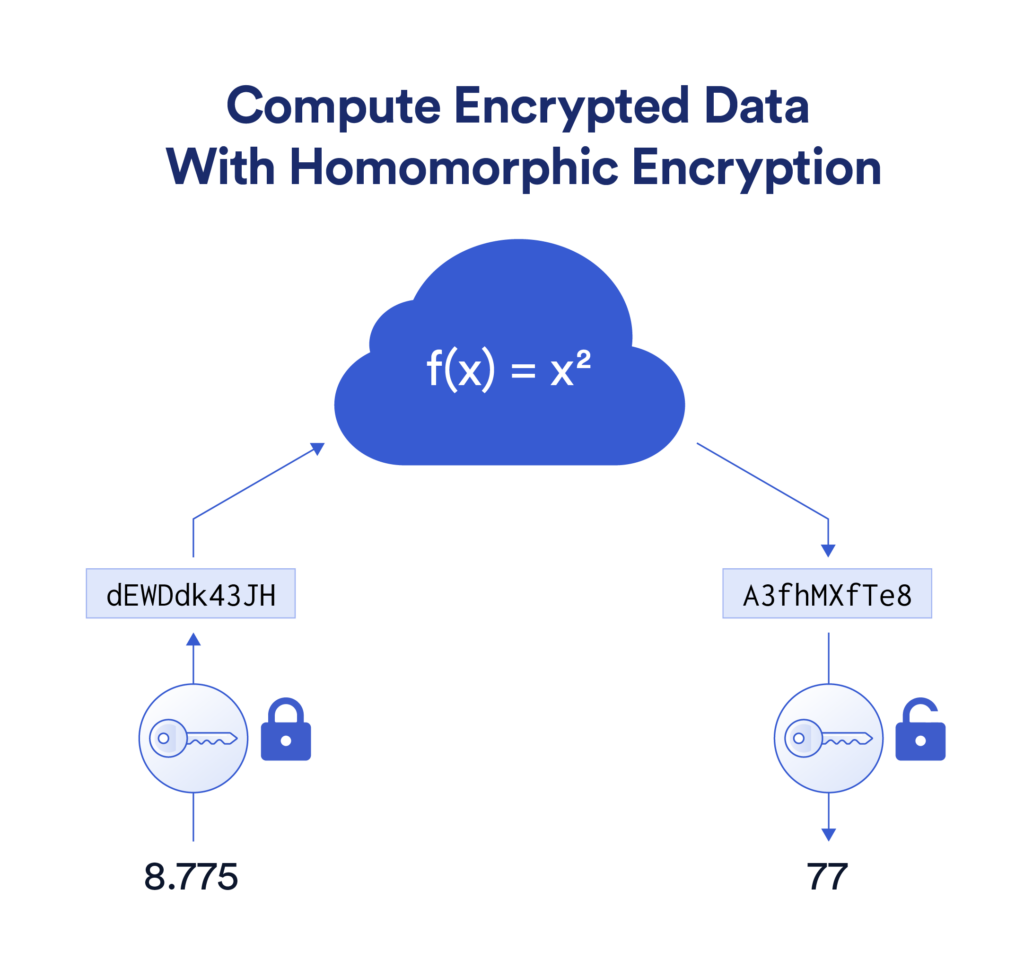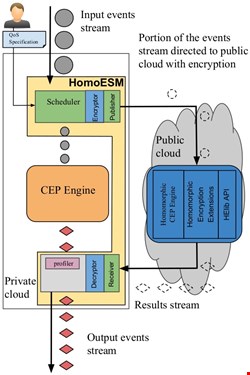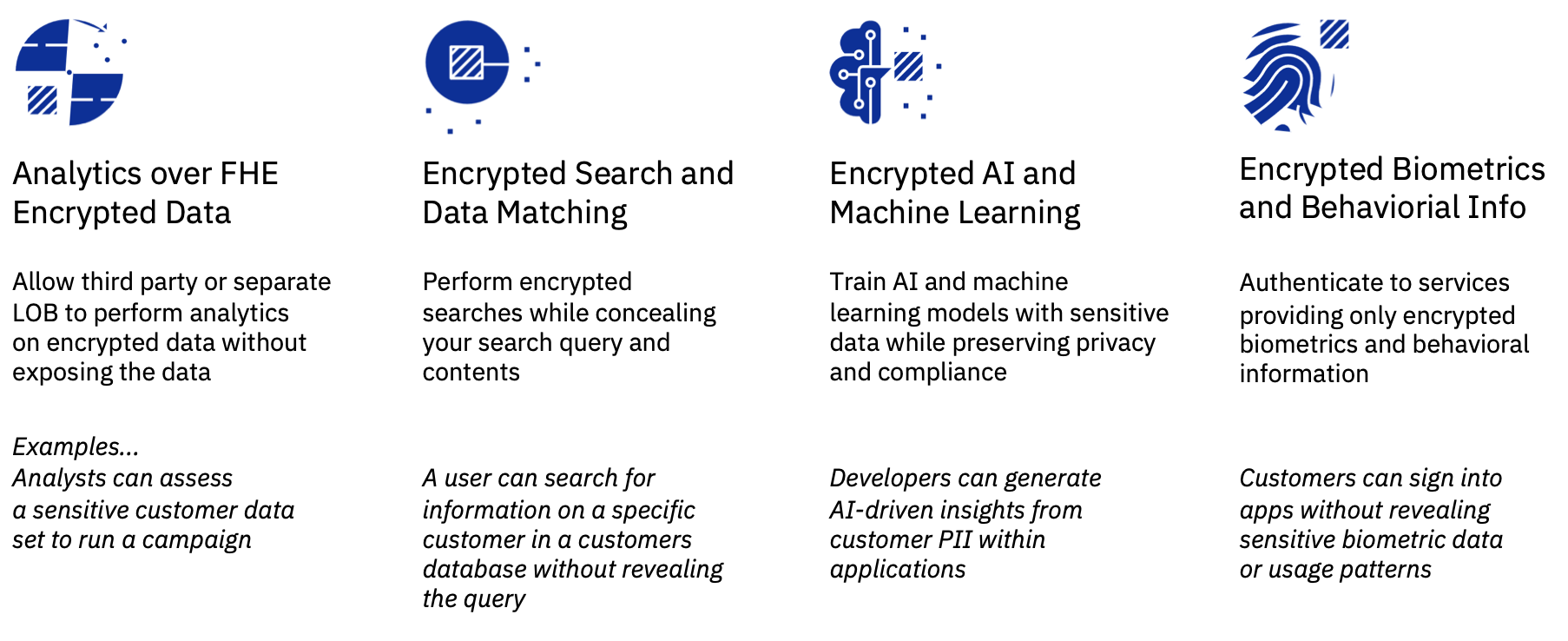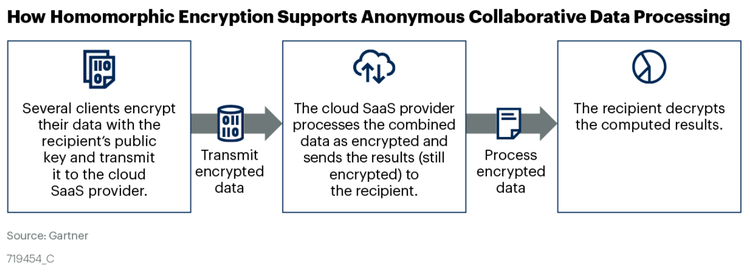
Inpher named in the 2020 Gartner Emerging Technologies: Homomorphic Encryption for Data Sharing With Privacy Report - Inpher

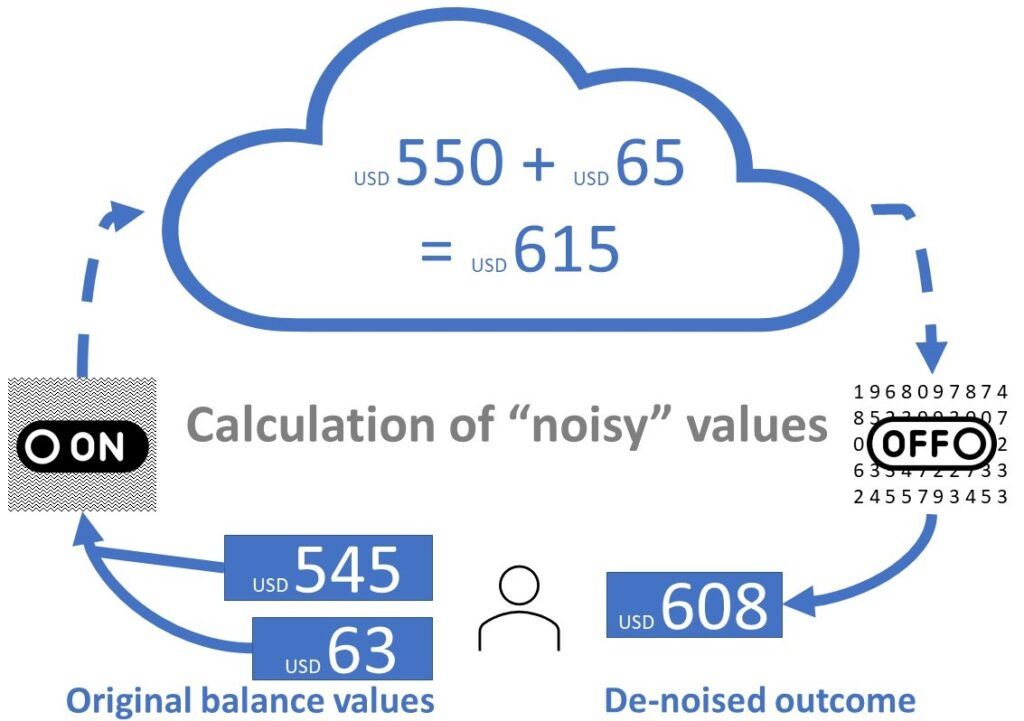
Homomorphic encryption, statistical machine learning and R software package – The Intelligence of Information

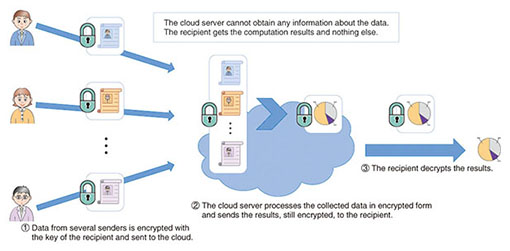
Privacy preserving service selection using fully homomorphic encryption scheme on untrusted cloud service platform - ScienceDirect
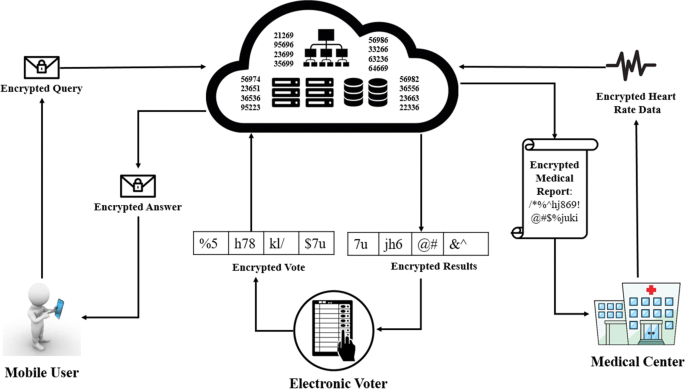
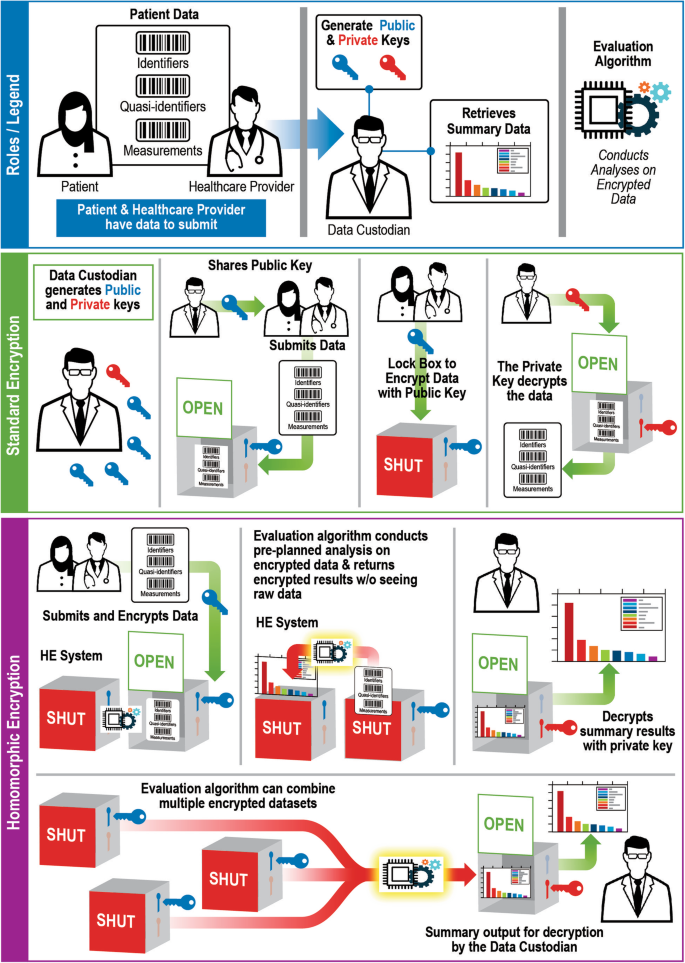
A systematic review of homomorphic encryption and its contributions in healthcare industry | SpringerLink
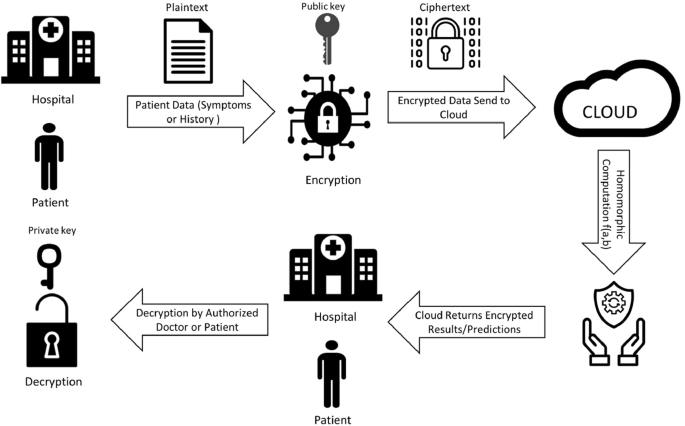
Proof-of-concept study: Homomorphically encrypted data can support real-time learning in personalized cancer medicine | BMC Medical Informatics and Decision Making | Full Text
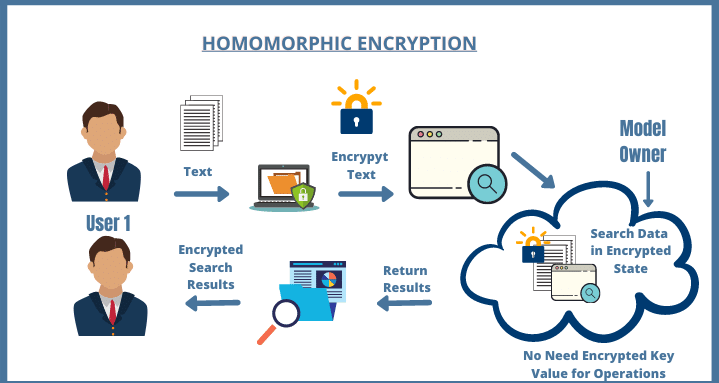
The Future of Secure Computation: A Comprehensive Guide to Homomorphic Encryption – Education in Future Technologies

JCP | Free Full-Text | Potential of Homomorphic Encryption for Cloud Computing Use Cases in Manufacturing

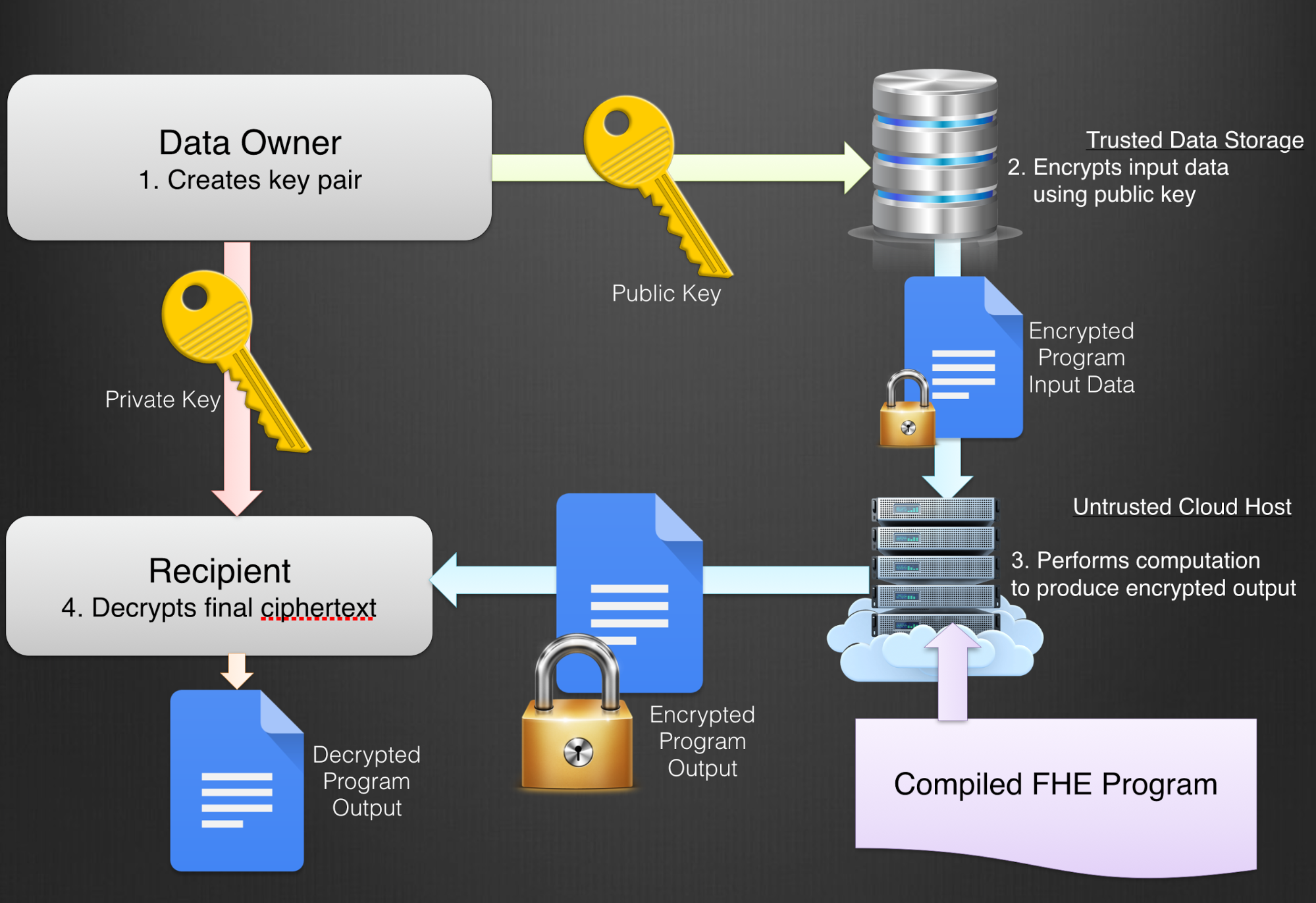
Google open-sources tools to bring fully homomorphic encryption into the mainstream | The Daily Swig
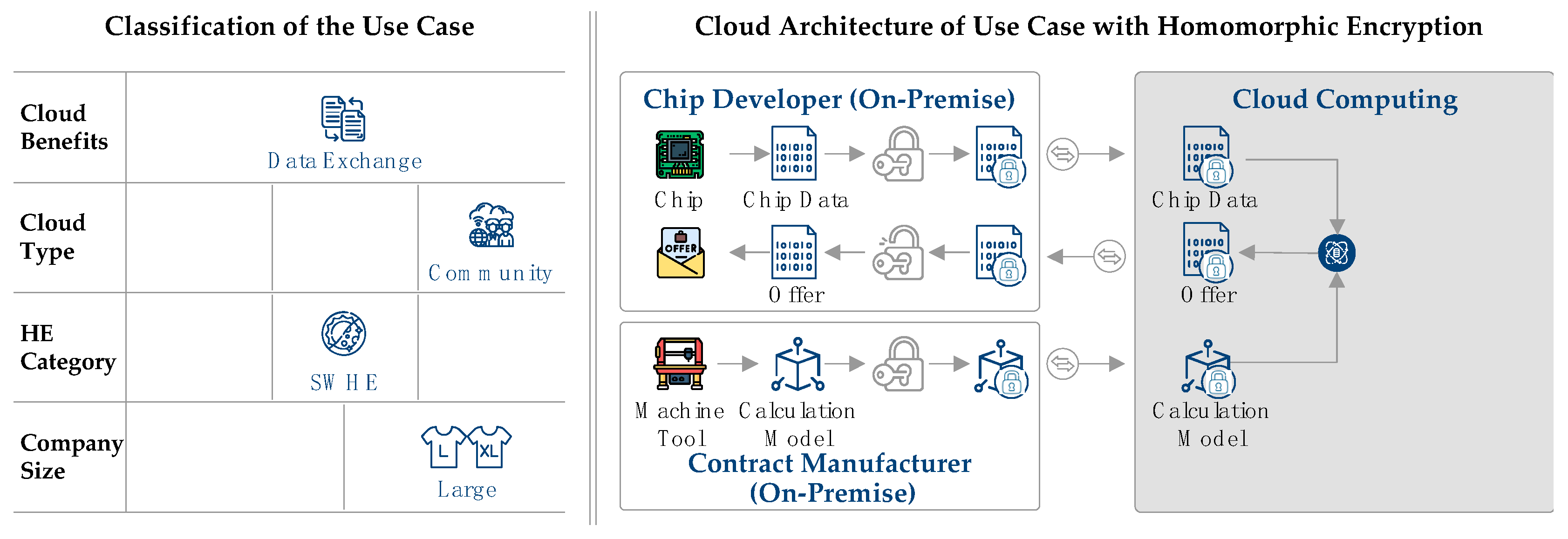
JCP | Free Full-Text | Potential of Homomorphic Encryption for Cloud Computing Use Cases in Manufacturing