
What are IoT search engines Shodan and Censys and what are they capable of | Kaspersky official blog

Shodan founder John Matherly on IoT security, dual-purpose hacking tools, and information overload | The Daily Swig
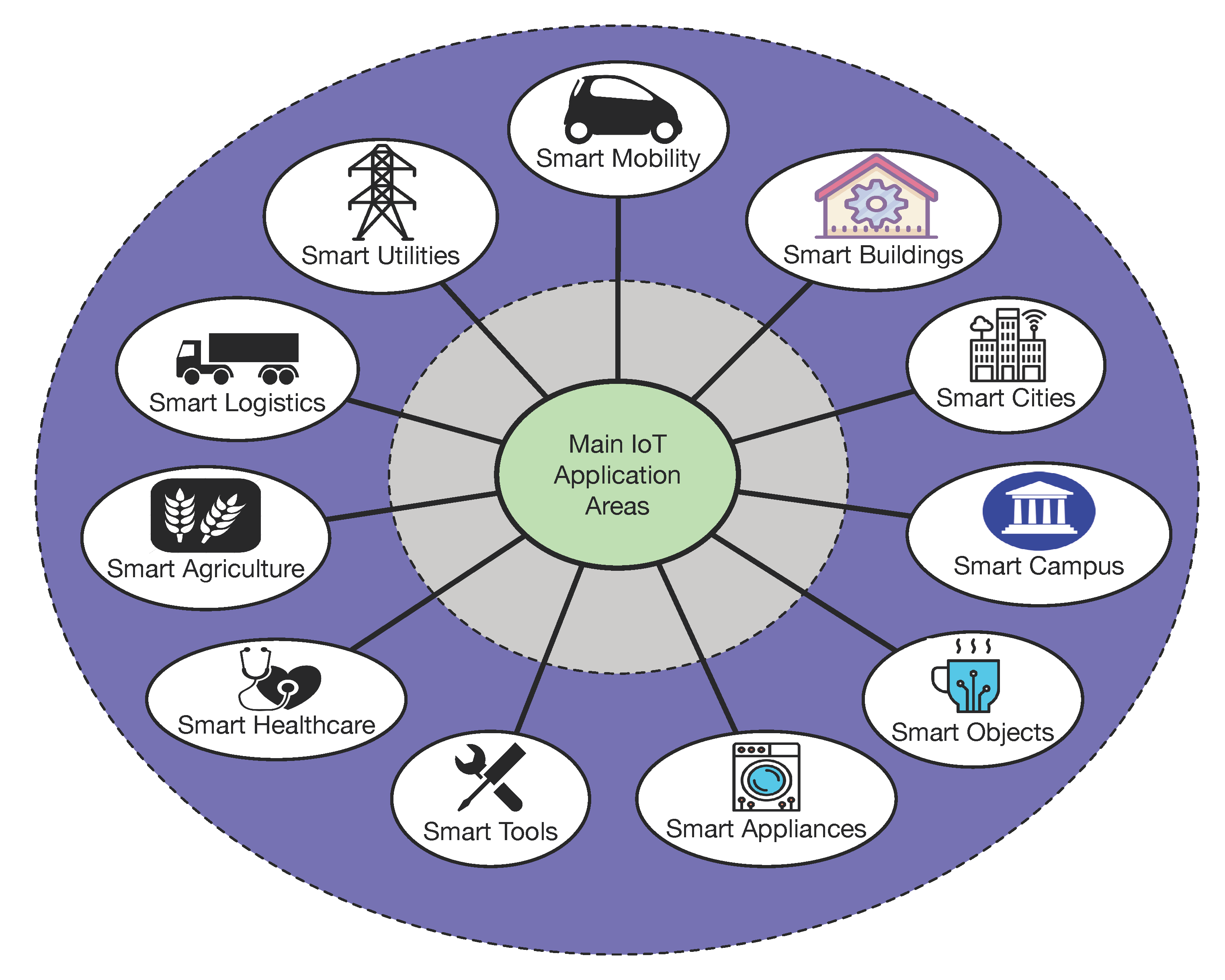
Sensors | Free Full-Text | Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases
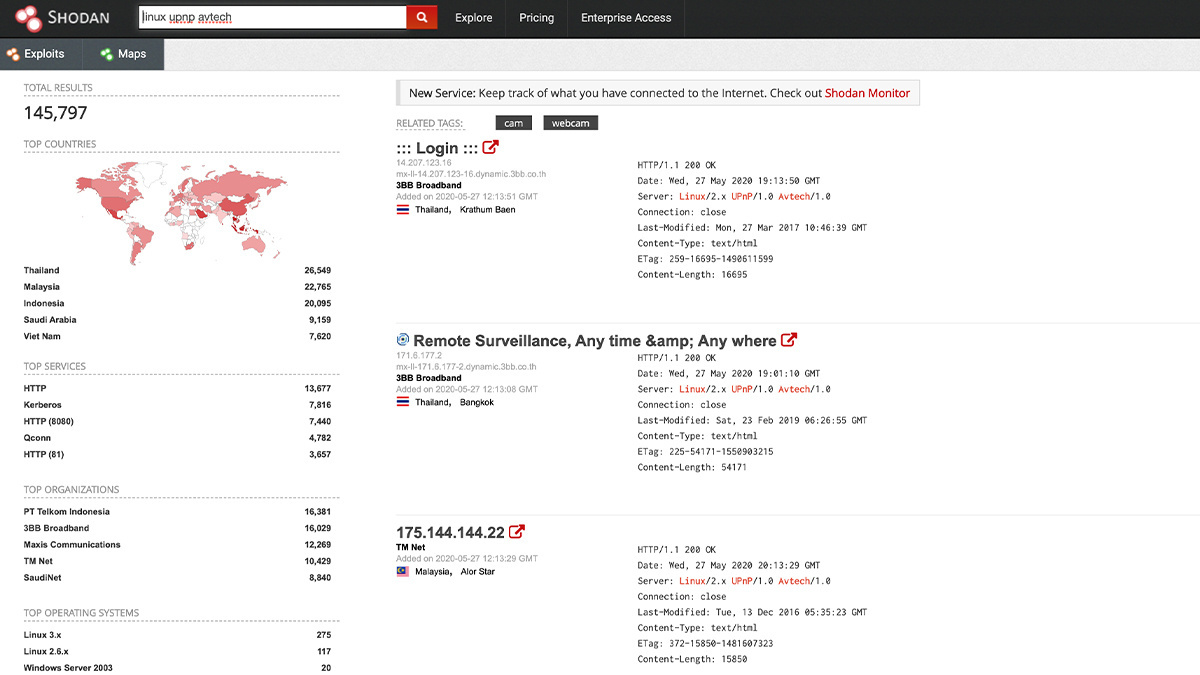
Shodan founder John Matherly on IoT security, dual-purpose hacking tools, and information overload | The Daily Swig

Shodan-based vulnerability assessment tool modular architecture. CPE,... | Download Scientific Diagram

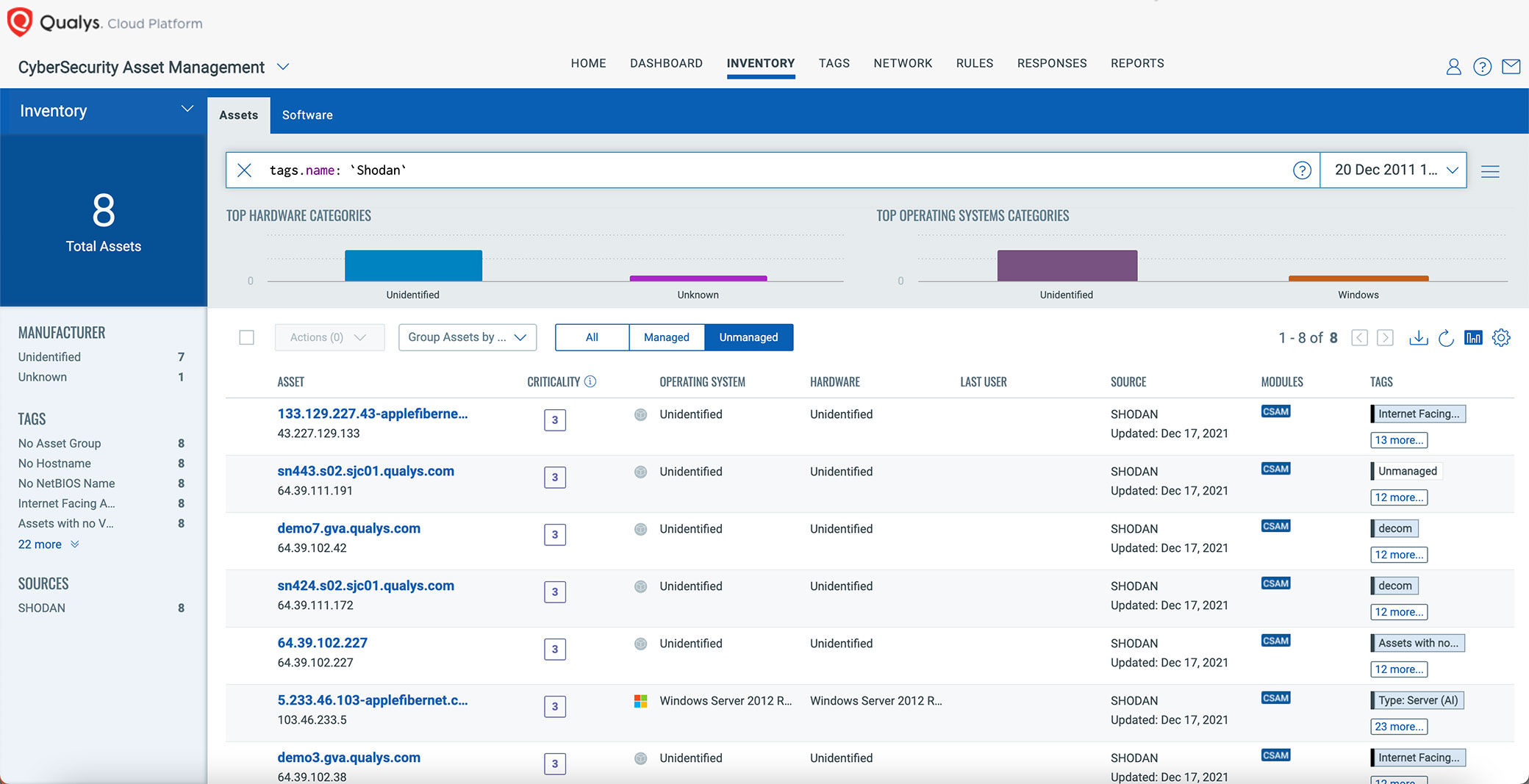

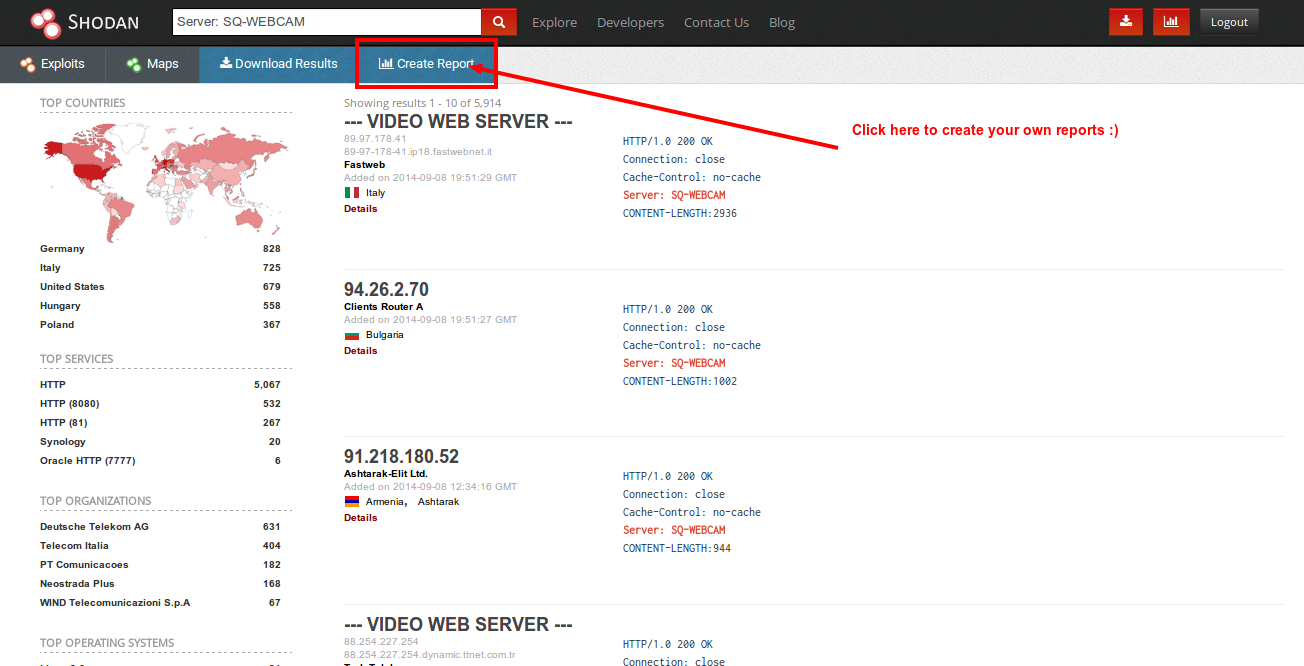

![What Is Shodan? How to Use It & How to Stay Protected [2023] What Is Shodan? How to Use It & How to Stay Protected [2023]](https://www.safetydetectives.com/wp-content/uploads/2021/04/what-is-shodan-1.png)
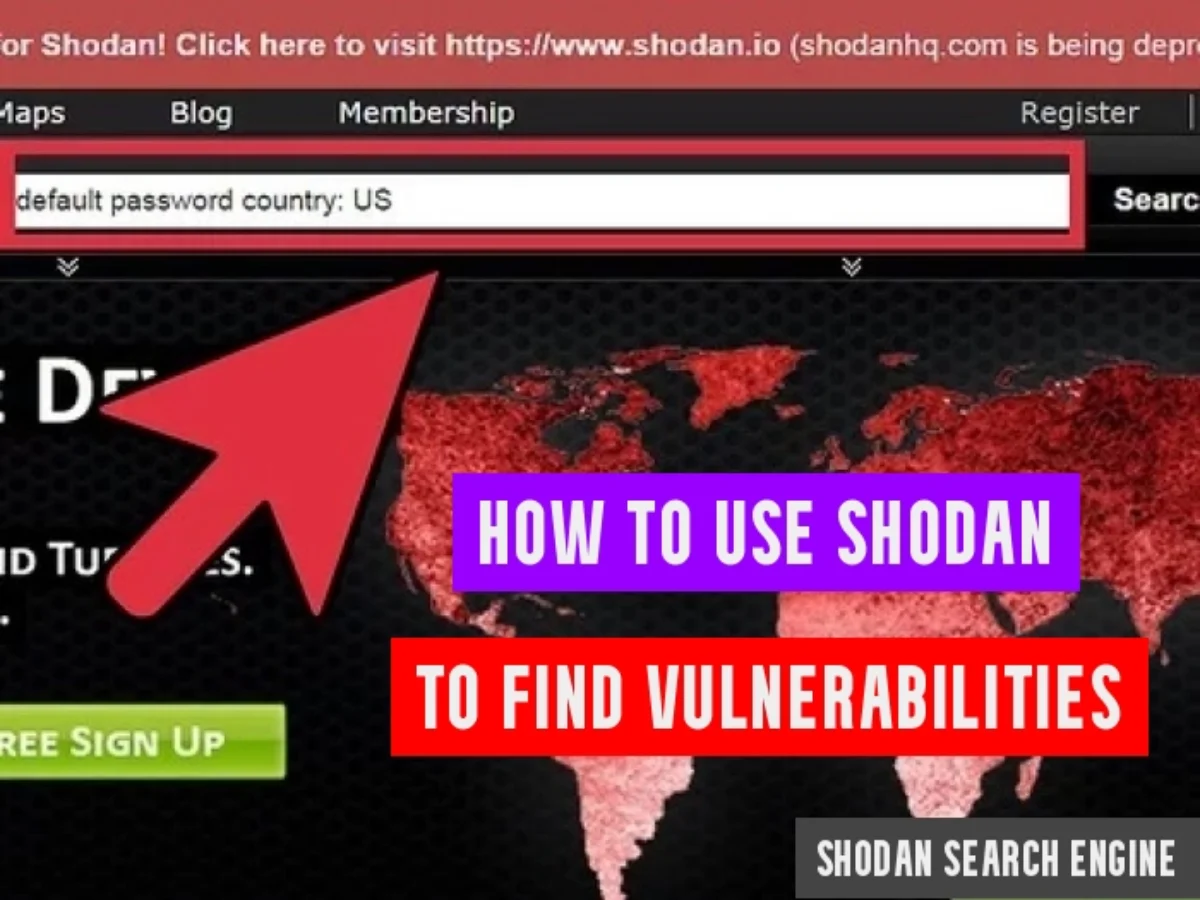
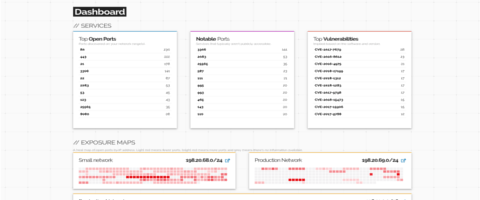

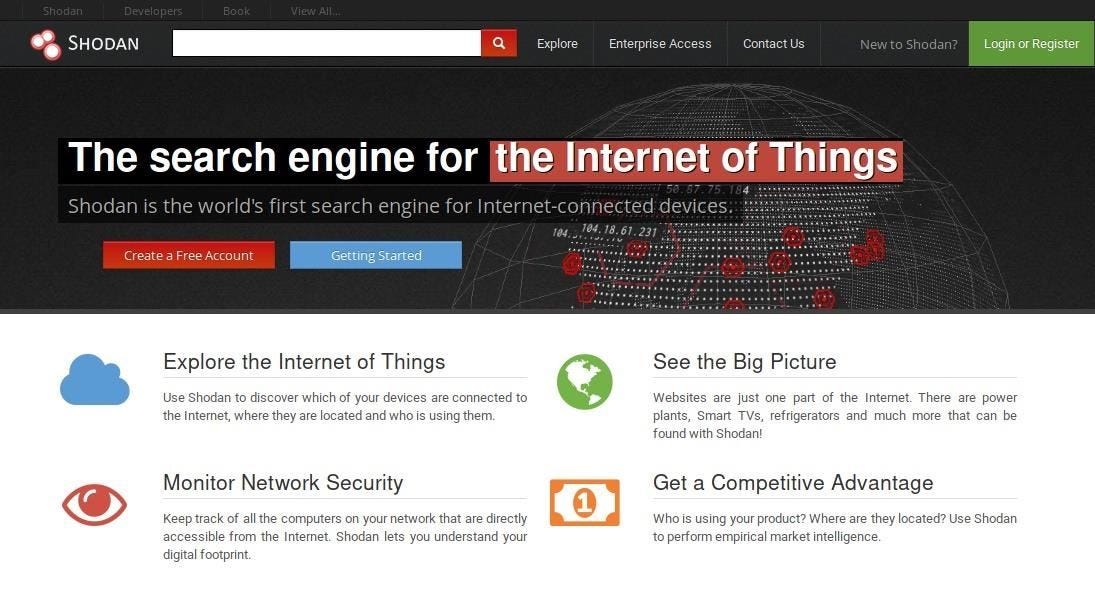
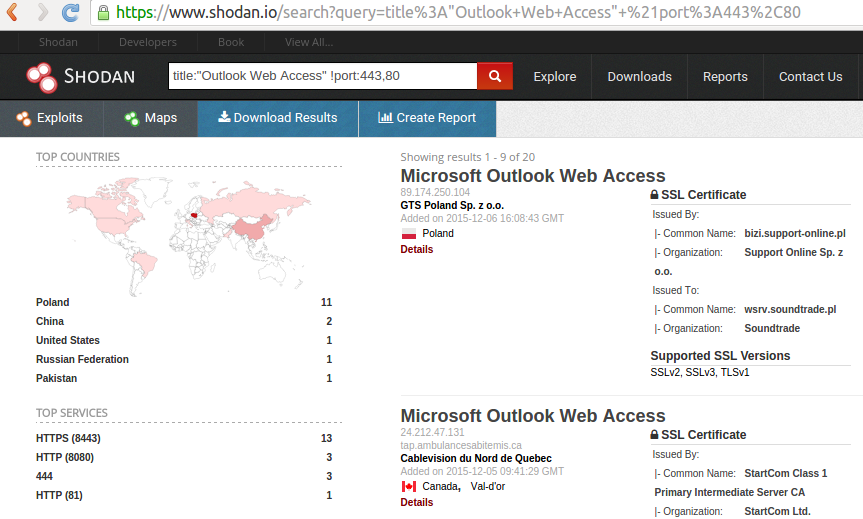
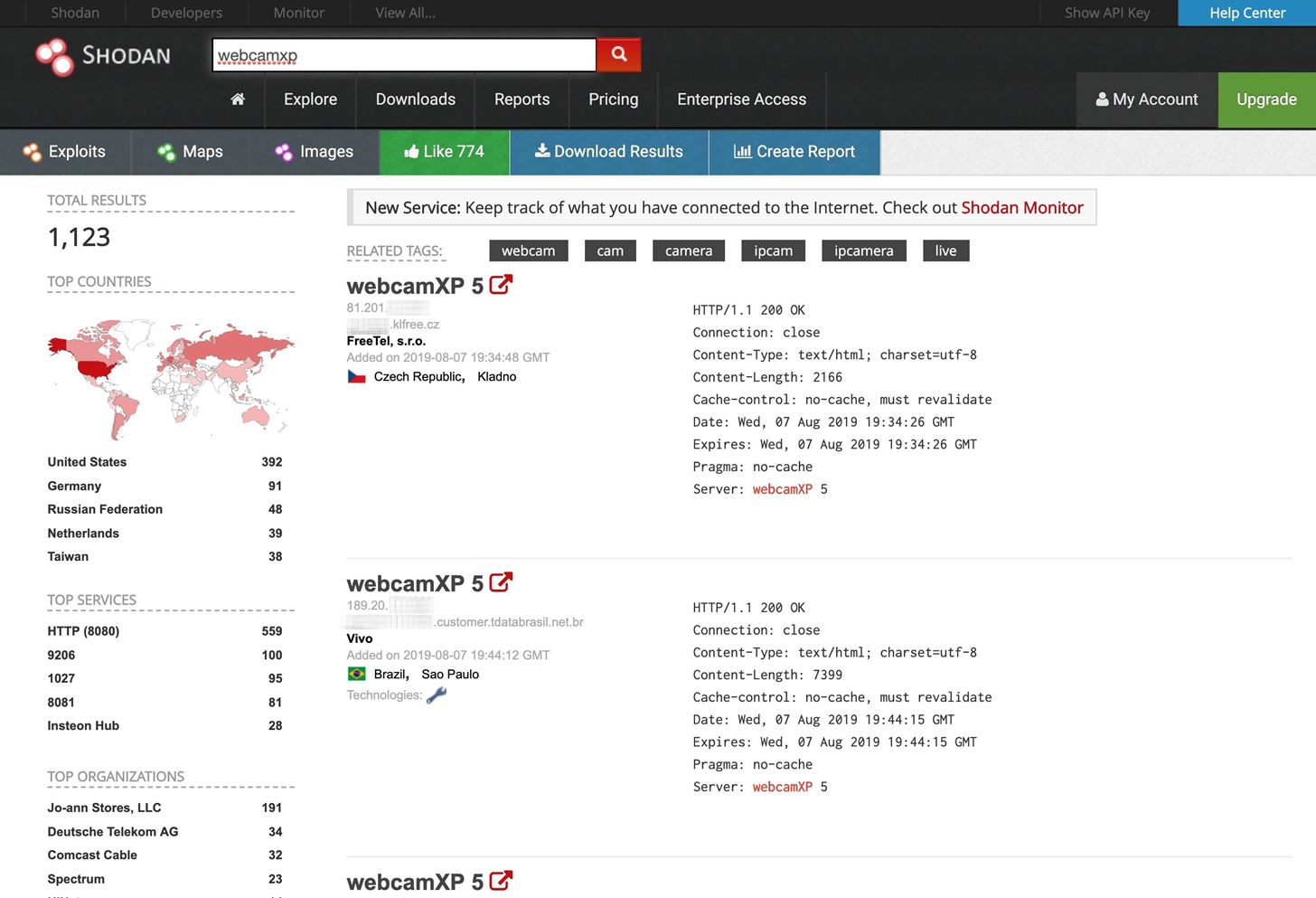


:quality(90)/images.vogel.de/vogelonline/bdb/1596900/1596944/original.jpg)